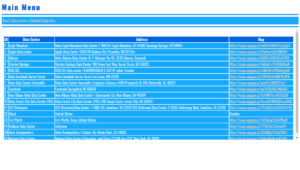
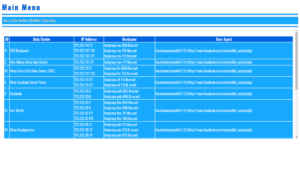
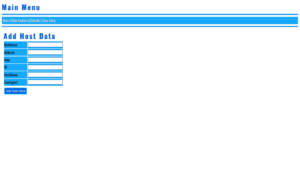
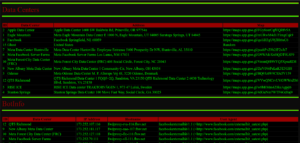
PHP Web Scraping Scripts
PHP Web Scraping Scripts:
Extracting Vast Data Types Efficiently
In today’s digital world, PHP web scraping scripts have become a powerful tool for extracting and organizing data from websites. PHP, known for its versatility and ease of use, allows developers to build efficient web scraping solutions that can handle a vast array of data types. Whether you’re looking to scrape text, images, videos, or product details, PHP-based scrapers can handle the task.
Diverse Data Types in Web Scraping
With PHP web scraping scripts, you can scrape various types of data, including:
- Text: Collect articles, blog posts, reviews, and product descriptions.
- Images and Videos: Extract visual content like photos, memes, icons, and embedded videos.
- Structured Data: Gather tables, charts, and metadata such as HTML tags, JSON, and XML.
- E-commerce Data: Scrape prices, product details, stock availability, and customer reviews from online stores.
This makes PHP a go-to choice for developers looking to extract a wide range of data types efficiently.
Current Technologies and Trends in PHP Web Scraping
Modern PHP web scraping scripts use libraries like cURL and Goutte for HTTP requests and DOMDocument or XPath for navigating HTML structures. In addition, headless browsers like Puppeteer and PhantomJS are being used in conjunction with PHP to render JavaScript-heavy websites, allowing for more comprehensive scraping of dynamic content.
Another trend is the rise of AI-enhanced scrapers, where machine learning algorithms are integrated to improve data accuracy and reduce errors. With the increasing need for automation and big data processing, PHP web scraping is evolving rapidly, offering solutions that are scalable and adaptable.
Harness the power of PHP web scraping to tap into the vast world of online data, and stay ahead in this ever-growing digital landscape.