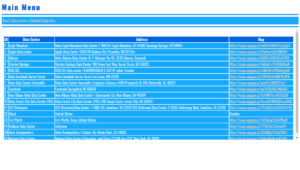
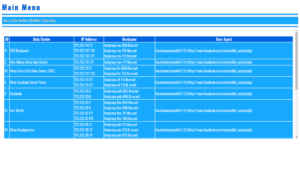
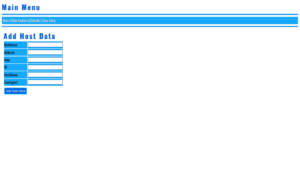
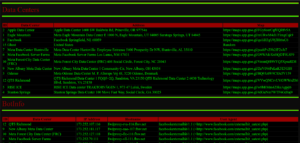
MySQL
What is MySQL?
MySQL is an open-source relational database management system (RDBMS) that is widely used for managing and organizing data in a structured manner. Developed and maintained by Oracle Corporation, MySQL uses Structured Query Language (SQL) to handle database tasks such as data retrieval, insertion, updating, and deletion.
What It’s Used For
MySQL is versatile and can be used in a variety of contexts:
- Web Applications: It’s commonly used in conjunction with PHP and Apache in the LAMP (Linux, Apache, MySQL, PHP/Perl/Python) stack for developing web applications.
- Data Storage: It stores data in a tabular format, which is suitable for applications requiring structured data storage, such as CRM systems, e-commerce sites, and content management systems (CMS).
- Analytics and Reporting: Businesses use MySQL to store and query large datasets, performing operations like complex joins, aggregations, and reporting.
- Application Development: Developers use MySQL for backend databases in applications due to its reliability and performance.
- Business Applications: It supports enterprise-level applications and ERP systems by managing large volumes of transactional data.
Institutions That Use MySQL
MySQL is used by a wide range of institutions:
- Tech Companies: Many tech giants and startups use MySQL, including Facebook, Twitter, and Google, for various internal systems and services.
- Educational Institutions: Universities and research organizations use MySQL for managing research data, student records, and educational content.
- Financial Institutions: Banks and financial services use MySQL for transactional data, customer management, and compliance-related applications.
- Government Agencies: Government departments use MySQL for managing public records, administrative data, and service delivery systems.
- Healthcare: Hospitals and clinics use MySQL for patient records, appointment scheduling, and medical data management.
Security and Vulnerabilities
Security:
- Access Control: MySQL supports user authentication and permissions, allowing administrators to control who can access or modify data.
- Encryption: It offers data-at-rest and data-in-transit encryption options to protect sensitive information.
- Audit Logging: It can log queries and changes to monitor and detect suspicious activity.
- Security Updates: Regular updates and patches are released to address security vulnerabilities.
Vulnerabilities:
- SQL Injection: Like other SQL-based systems, MySQL can be vulnerable to SQL injection attacks if applications do not properly sanitize user input.
- Misconfigurations: Incorrectly configured MySQL installations can lead to security issues, such as unauthorized data access.
- Outdated Versions: Running outdated versions without the latest security patches can expose the database to known vulnerabilities.
- Backup Security: If not properly secured, backup files can be a target for data breaches.
Resources
Here are some useful resources for learning more about MySQL:
- MySQL Official Website – The main site for downloads, documentation, and product information.
- MySQL Documentation – Comprehensive documentation covering installation, configuration, and usage.
- MySQL Tutorial – A resource for learning MySQL through tutorials and examples.
- MySQL Forums – A place to ask questions and engage with the MySQL community.
- MySQL Security Best Practices – Guidelines and recommendations for securing MySQL installations.
This overview should give you a solid understanding of MySQL, its uses, and its security aspects.